According to a recent study from Ivanti, 70% of employees are using their personal devices for work, even when it violates company “Bring Your Own Device” (BYOD) policy. Using your own device sounds harmless, right? You are getting the job done and that’s all that matters. This however illustrates two underline issue of an organization; which is they have not built the infrastructure or provided the tools that employees need to do their jobs nor do they have the proper data protection and cybersecurity policy in mind.
Ignoring this problem is taking a risk with data, employees and a company’s reputation.
Why Employees Use Personal Devices
When employee flips open their own laptop or phone for work, it’s not just a convenience, it’s a symptom of:
- The company has not funded or provided the right equipment, software or platforms for employee use.
- The expectation is high (create content, generate results, meet tight deadlines) but the support is low (no proper hardware, no workflow defined).
- Skilled employees have existing tools and subscriptions they are comfortable with, so they default to those rather than wait because the job needs to be done.
This behavior does not mean everyone is trying to sneak around policy; it means a company has not built a work environment that makes sense. Bring Your Own Device (BYOD) is not wrong, but when it happens because of the lack of understanding what your people need, what their workflows are; not knowing these things translate into underinvesting in your own operation.
If you don’t map out what your workforce needs (hardware, software, time, training), you end up letting the details dictate the direction and employees adopt workarounds.
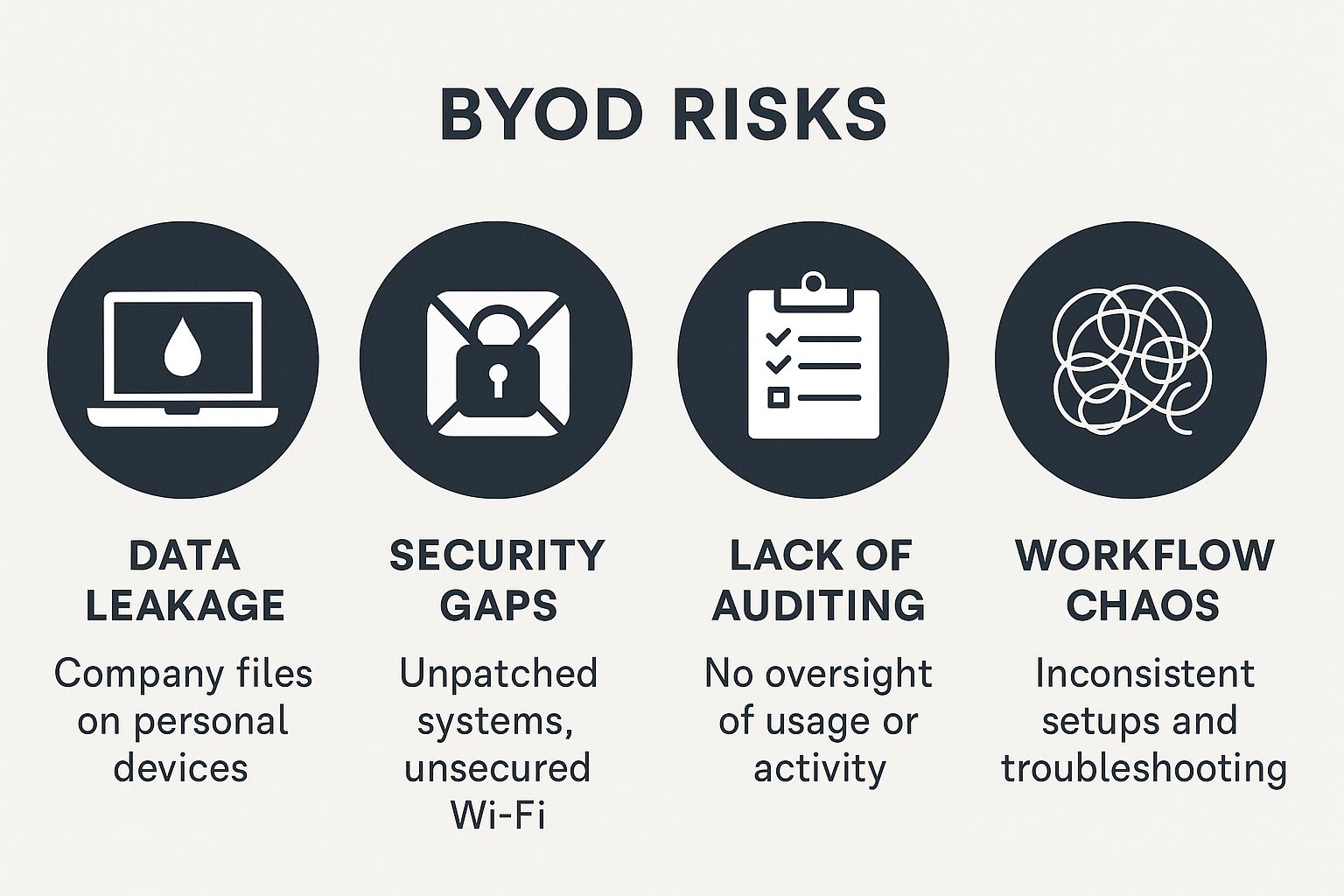
The Risks of Unmanaged BYOD
When your people are on personal devices, you introduce a host of risks both obvious and hidden. These include:
- Data leakage: company files on personal computers, unsupervised backups or cloud syncs.
- Security gaps: older OS versions, unsecured Wi-Fi, no standard patches or endpoint security management.
- Lack of auditing: no clear way to see what device is doing what, when, how.
- Workflow chaos: because each person uses a different setup, support and troubleshooting become inconsistent.
- Burnout/overwork: when you expect big outputs but don’t give big inputs (tools, time, infrastructure), you are pushing people beyond logical limits.
If you are seeing any of these problems, lack of authority over your tech stack or data incidents, take this as a sign.
How to Fix Your BYOD Policy
You can’t just turn away and hope the next device purchase solves everything. You need a realistic plan. Here are practical steps:
- Audit Your Current State
- List what devices and services employees are using. This includes official and unofficial.
- Map out the workflows: who’s creating what, how long it takes, what tools they use. This gives you an understanding of how long projects takes and understand employee’s processes.
- Include mobile workforce security factors to assess data protection levels.
- Set Clear Standards
- Define minimum Bring Your Own Device (BYOD) policy requirements if you allow it: secure access, approved software, patch requirements.
- Decide if you will provide the devices: specify specs, support rules, refresh cycles.
- Make sure you have IT governance and cybersecurity policy expectations that are mandatory and followed.
- Budget for Infrastructure
- Allocate funds for hardware, software licenses, and device management software.
- Include training and support; work isn’t just about output; it’s about sustainable processes.
- Communicate with Your Team
- Ask employees what they need. Let them show how they work.
- Make clear the what, why, and how: “Here’s what we are giving, here’s what we expect, here’s how we will support you.”
- Whatever you provide, realize that output is based on what infrastructure and tools you supplied. Do not expect results greater than that.
- Monitor and Improve
- After rollout, check: Are people still using personal devices? Why?
- Review employee device compliance and endpoint security status.
- Are security incidents up or down? Are workflows smoother or still chaotic? Adjust as needed.
Just Know
If you allow employees to use personal devices because you choose to, that’s one thing. But if it’s because you have not built the infrastructure they need, you are choosing risk. Fix the foundation, strengthen your BYOD policy and lead with IT governance that protects your employees and your data.
____________________________________________________________________________________________________________________________________
Shaunta Garth is a Strategic Communications & Visibility Architect specializing in digital storytelling, media strategy and public affairs.